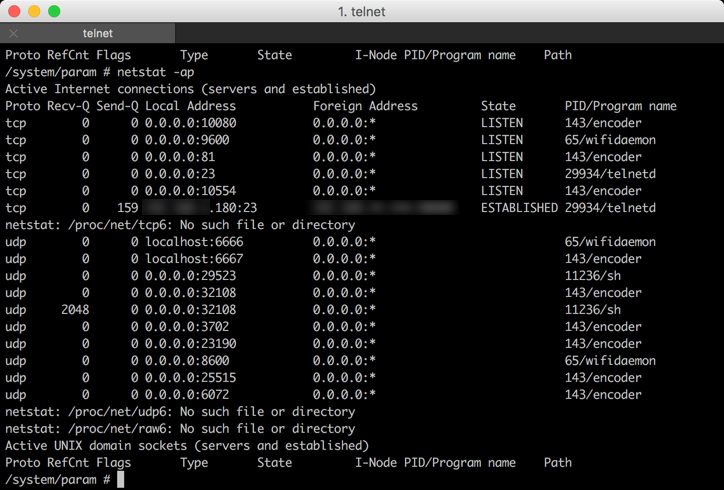
Ouvis veezon VZ1 Hacking ( and clones alike )
When I first bought this camera, I read the reviews from all the people that complained their camara got hack because they left the default (no pass) password, and someone took control over their cam. Been a bit savvy and having a “decent” firewall (Fortigate) at home, the first thing I did when connecting the camera to my home is to look at all the active connections the device was trying to make. Lets look into it.
The camera software claimed it didn’t need the IP of the device, just a qr code that would pair the camera with the app on my phone. From the screenshot below it looks like it’s a UDP tunnel, but keep in mind I don’t have upnp enabled, so it’s probably using some magic to connect the 2 devices through UDP.
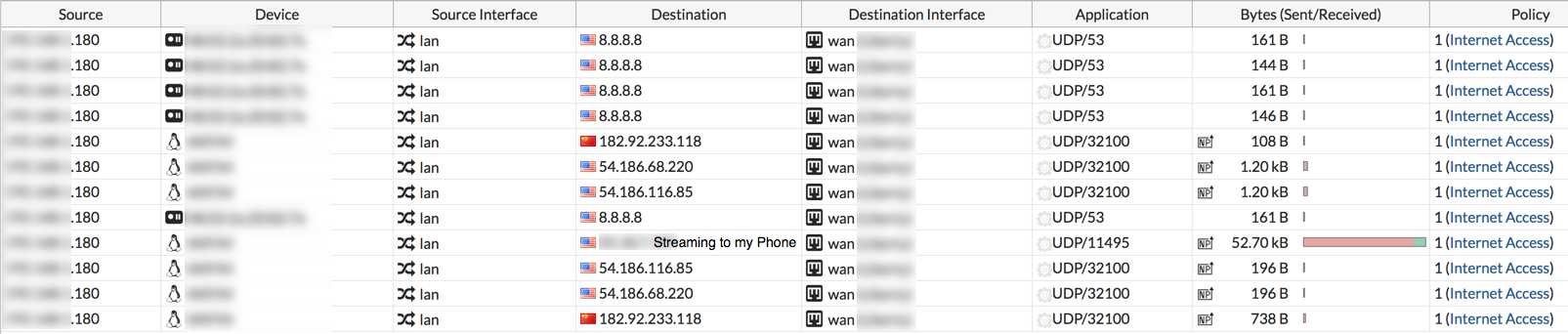
The other connections are:
8.8.8.8 = Google DNS
54.186.68.220 = AWS server on port 32100
54.186.116.85 =AWS server on port 32100
182.92.233.118 = Chinnese IP on port 32100 ( I blocked it for now and all functions still work. )
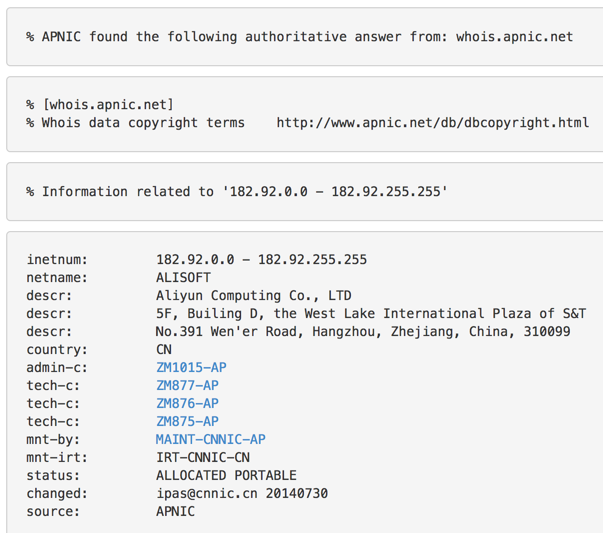
Looking a bit more into the chinese ip it looks like from Aliyun Computing. A quick google search tells me it seems aliyun is the chinese counter part of Amazon AWS services, it seem like Aliuyun is now Alibaba Cloud services.
Looking at the communication generate from the app on my phone. It seems the trick the camera uses to have both devices to connect to a third party device, that will help out do a UDP Pinhole between both devices to connect directly via UDP without doing port forwarding.
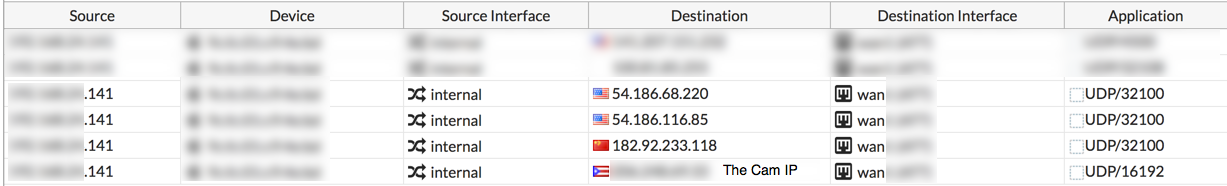
For now I blocked access to the for the China IP and keep an eye on what traffic goes on the system. Based on the research the encoder process is the one that connect between devices, but i’m worried about the sh process listening on those udp ports.